1. 문제
https://dreamhack.io/wargame/challenges/24/
simple_sqli
로그인 서비스입니다. SQL INJECTION 취약점을 통해 플래그를 획득하세요. 플래그는 flag.txt, FLAG 변수에 있습니다. Reference Server-side Basic
dreamhack.io
2. 해결 과정
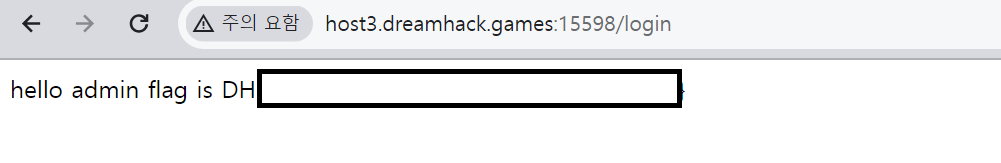
조건문에 userid 가 'admin' 이고, 패스워드를 입력하면 FLAG 를 리턴한다고 되어있다.
이때, userid만 제대로 admin으로 주고 그 뒤의 쿼리를 주석처리하면 admin에 접근할 수 있다.
@app.route('/login', methods=['GET', 'POST'])
def login():
if request.method == 'GET':
return render_template('login.html')
else:
userid = request.form.get('userid')
userpassword = request.form.get('userpassword')
res = query_db(f'select * from users where userid="{userid}" and userpassword="{userpassword}"')
if res:
userid = res[0]
if userid == 'admin':
return f'hello {userid} flag is {FLAG}'
return f'<script>alert("hello {userid}");history.go(-1);</script>'
return '<script>alert("wrong");history.go(-1);</script>'
성공